As i have started a journey into vulnerability research and exploitation, i thought of sharing some topics which I found very confusing initially. So i will try to detail as much information as possible.
So we will begin by writing a simple helloworld assembly code. The code will do the following
Now that i have given you a brief idea on why we need to write an exit code in asm, we will program a helloworld code
Now that I have a working , elf binary , my next target is to generate the shellcode from it.
I will use the objdump utility to view the disassembled contents of the binary along with the opcodes.
So we will begin by writing a simple helloworld assembly code. The code will do the following
- Print HelloWorld
- and Exit
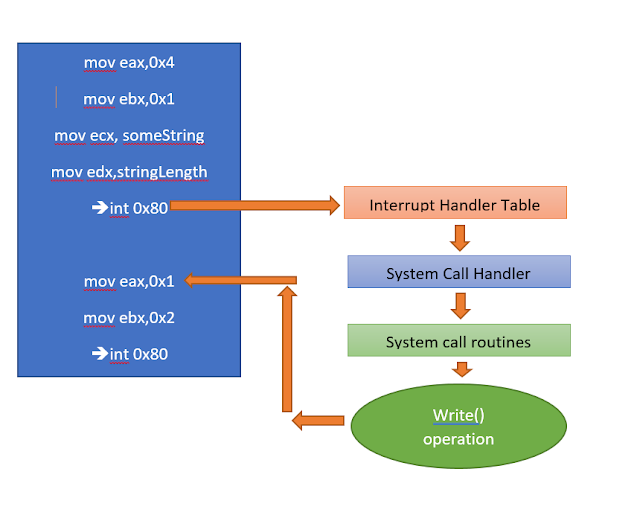
Now you may wonder why do I have to write a code that exits ? If such is the case then you might probably have written good amount of code in high level language. The compilers of high level languages takes care of it i.e writing the extra code in the object file like the exit code. Internally every operations like read , write , exit and so on requires some low level calls to kernel. These calls are called SysCalls. So if you are programming using high level language like C and C++ , then you don't need to write codes to make the syscalls because due to the abstraction layer that hides the excessive code that is required to code. The compiler takes care to generate the object code which has essential exit code in it. To trigger these syscalls we need to use interrupt. Now these interrupt is maintained using an interrupt table. The diagram below shows the workflow of the syscalls and the interrupt
Now that i have given you a brief idea on why we need to write an exit code in asm, we will program a helloworld code
Now that I have a working , elf binary , my next target is to generate the shellcode from it.
I will use the objdump utility to view the disassembled contents of the binary along with the opcodes.
There is a nice one liner at ( http://www.commandlinefu.com/commands/view/6051/get-all-shellcode-on-binary-file-from-objdump ) which we can use to get the shellcode from the binary.
objdump -d ./PROGRAM|grep '[0-9a-f]:'|grep -v 'file'|cut -f2 -d:|cut -f1-6 -d' '|tr -s ' '|tr '\t' ' '|sed 's/ $//g'|sed 's/ /\\x/g'|paste -d '' -s |sed 's/^/"/'|sed 's/$/"/g'
Using this technique, we can get a nice shell code from it which we dont need to extract manually from the disassembled code
Sweet! Now our 1st part of the tutorial is over , moving to the next , ShellCode to Assembly.
Now if I present you with the following shellcode, how will you get back to a working elf executable.
"\xb8\x04\x00\x00\x00\xbb\x01\x00\x00\x00\xb9\xa4\x90\x04\x08\xba\x10\x00\x00\x00\xcd\x80\xb8\x01\x00\x00\x00\xbb\x02\x00\x00\x00\xcd\x80"'
Lets copy the shellcode and save the contents inside a file. Please note we are going to save the shellcode as raw hex file and not as text. To do it we need help of perl
Syntax : perl -e 'print "YOUR SHELL CODE"' > outputFile
perl -e 'print "\xb8\x04\x00\x00\x00\xbb\x01\x00\x00\x00\xb9\xa4\x90\x04\x08\xba\x10\x00\x00\x00\xcd\x80\xb8\x01\x00\x00\x00\xbb\x02\x00\x00\x00\xcd\x80"' > hexraw
Now we will use the ndisasm utility to get the disassembled code from the file. So what ndisasm is doing here is converting the hex opcodes into equivalent asm instructions.
Syntax : ndisasm -b 32 hexraw
Now you can see , we almost have the same code that we wrote, except there is an hardcoded address 0x80490a4 at line 3 and hardcoded value at line 4. The problem is we got the disassembled code of the .text section and not the .data section. Let us fix the code by modifying the code a little.
Finally we are able to get back our ASM code and make it execute successfully
References:
https://en.wikipedia.org/wiki/System_call
https://www.youtube.com/watch?v=G4wA7Zm-DIU&feature=youtu.be
http://searchsecurity.techtarget.com/answer/What-is-the-relationship-between-shellcode-and-exploit-code
https://en.wikipedia.org/wiki/System_call
https://www.youtube.com/watch?v=G4wA7Zm-DIU&feature=youtu.be
http://searchsecurity.techtarget.com/answer/What-is-the-relationship-between-shellcode-and-exploit-code